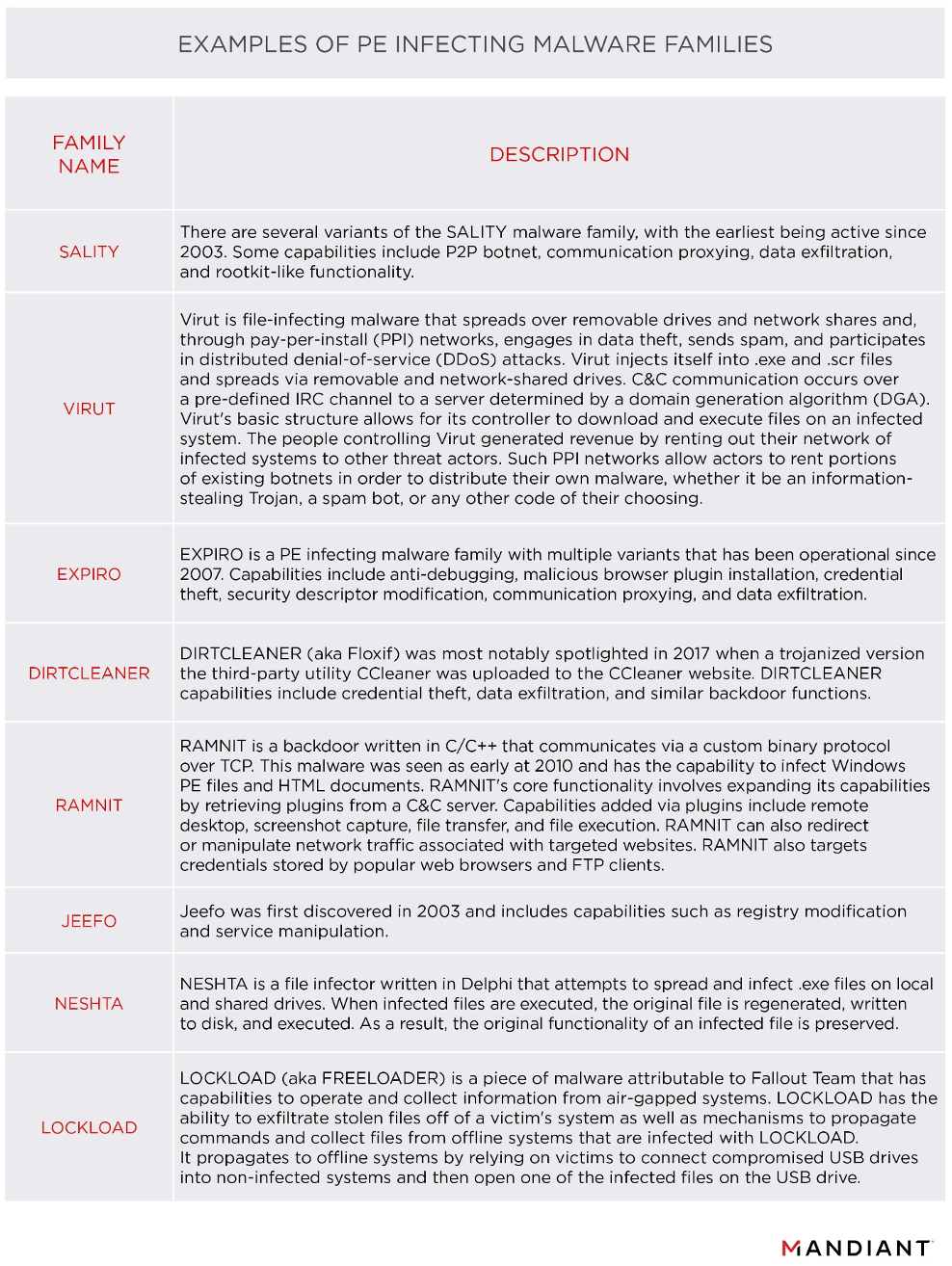
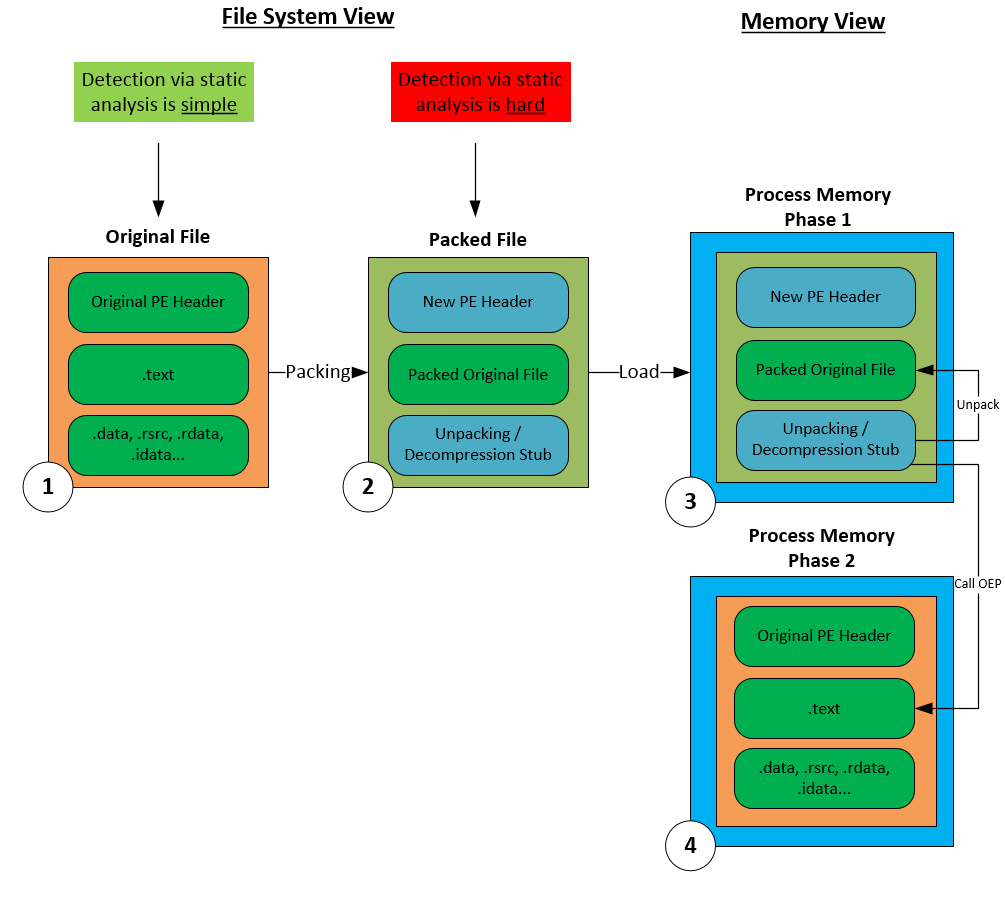
GitHub - ryderling/adversarial-attacks-and-defenses-for-windows-pe-malware-detection: A curated resource list of adversarial attacks and defenses for Windows PE malware detection.
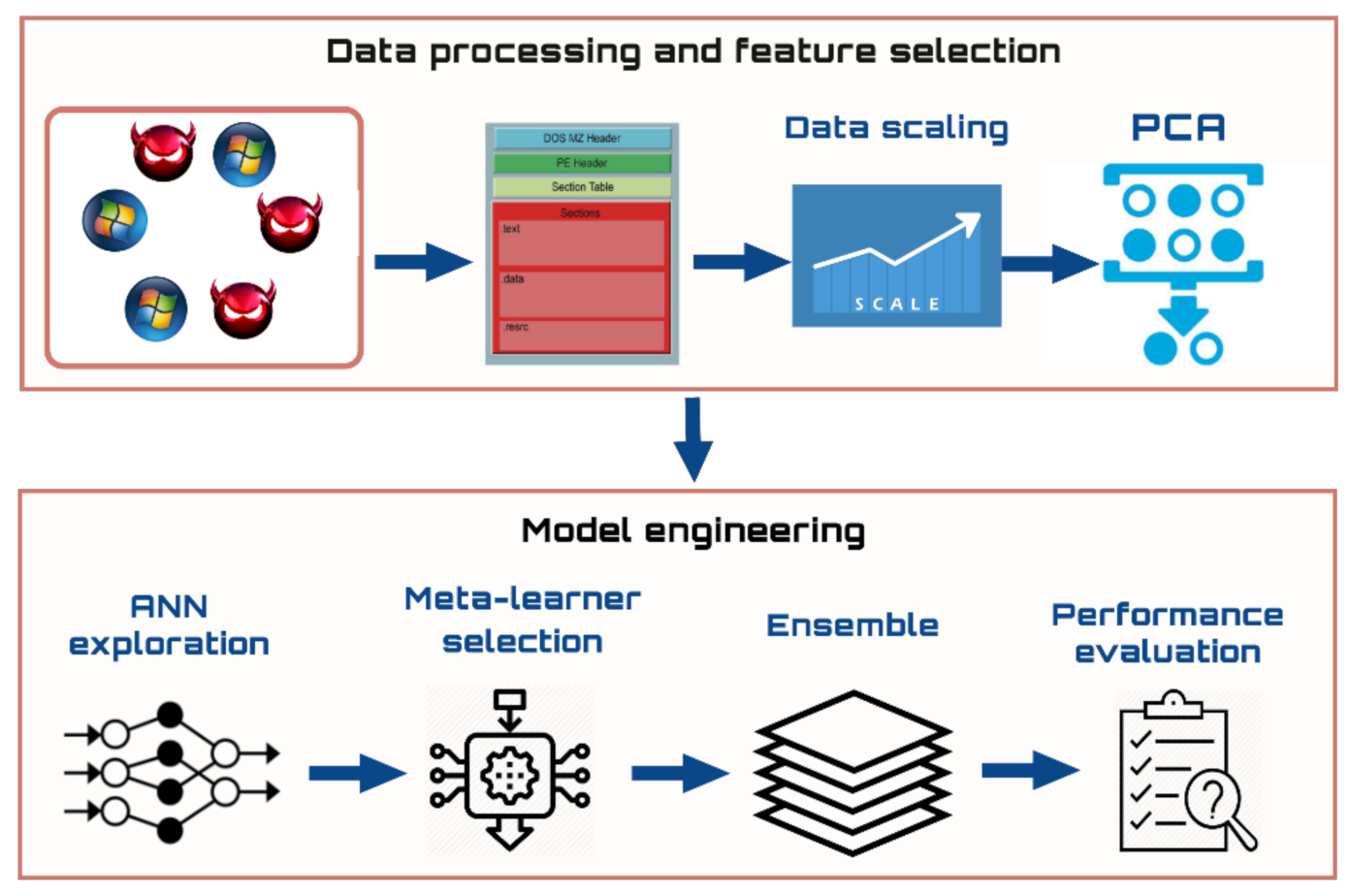
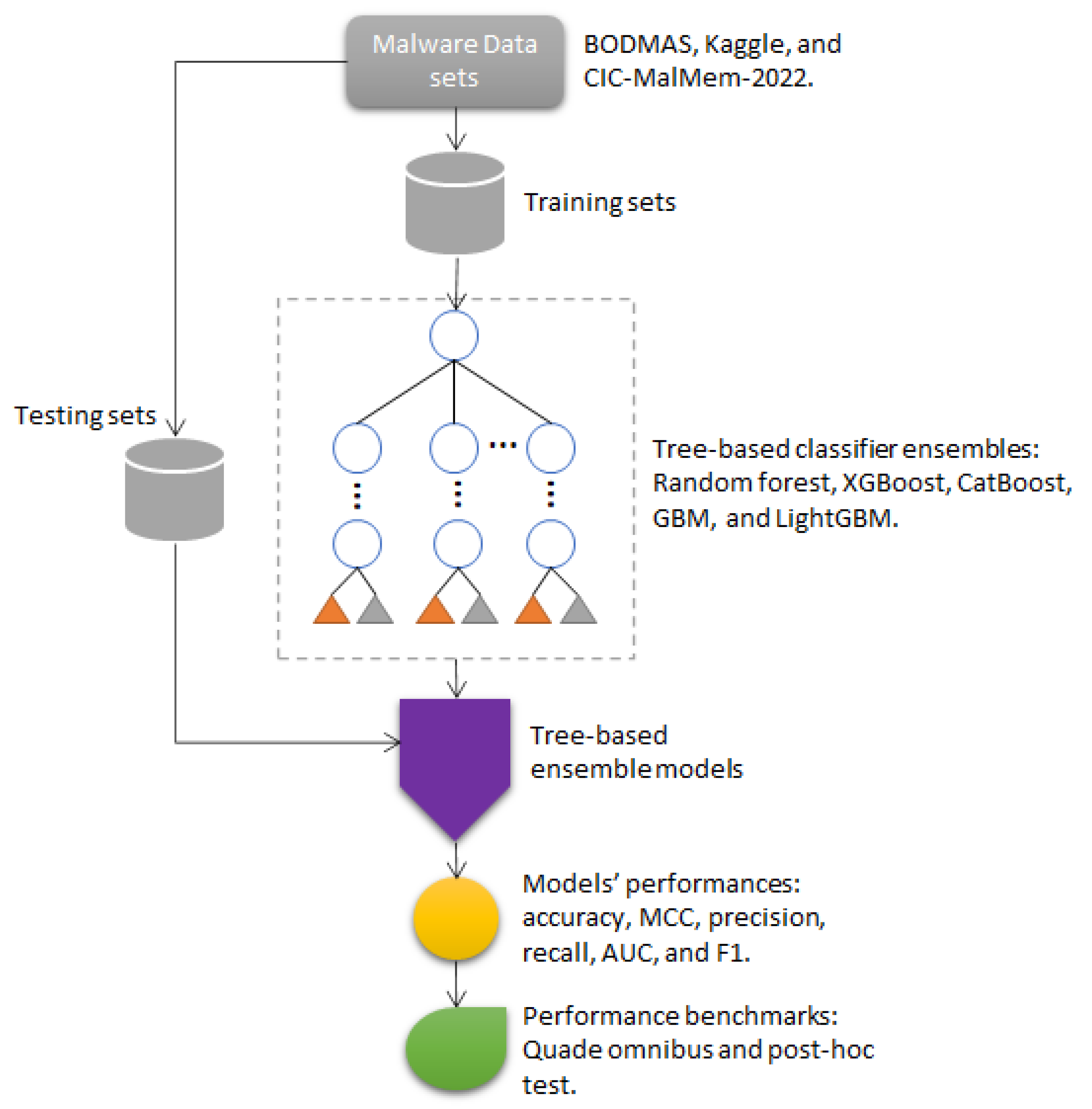
Electronics | Free Full-Text | Ensemble-Based Classification Using Neural Networks and Machine Learning Models for Windows PE Malware Detection